Keamanan komputer menurut para ahli – Computer security, according to experts, is a multifaceted domain that safeguards our digital realm from a plethora of threats. This article delves into the intricacies of cybersecurity, exploring best practices, emerging trends, and industry-recognized frameworks to empower individuals and organizations in navigating the ever-evolving cyber landscape.
Threats such as malware, viruses, and phishing attacks pose significant risks, while ransomware and data breaches can have devastating consequences. To combat these threats, experts emphasize the importance of strong passwords, firewalls, antivirus software, and regular software updates and backups.
Threats to Computer Security
Computer security threats are a constant concern for individuals and organizations alike. Understanding the different types of threats and their potential impact is crucial for implementing effective security measures.
Malware
Malware, short for malicious software, encompasses a wide range of threats that can harm computers and networks. Viruses, worms, and Trojan horses are common types of malware. Viruses attach themselves to legitimate programs and spread when the infected program is executed, while worms exploit vulnerabilities in software to self-replicate and spread across networks.
Trojan horses disguise themselves as legitimate software to trick users into installing them, providing attackers with remote access to the infected system.
Phishing Attacks
Phishing attacks attempt to trick users into revealing sensitive information, such as passwords or credit card numbers, by sending fraudulent emails or creating fake websites that mimic legitimate ones. These attacks often use social engineering techniques to manipulate users into clicking on malicious links or providing their personal data.
Ransomware
Ransomware is a particularly damaging type of malware that encrypts a victim’s files and demands a ransom payment in exchange for decrypting them. Ransomware attacks can have severe consequences for businesses and individuals, as they can lead to data loss, operational disruptions, and financial losses.
Data Breaches
Data breaches occur when unauthorized individuals gain access to sensitive information, such as personal data, financial records, or intellectual property. Data breaches can result from various security vulnerabilities, including weak passwords, unpatched software, or social engineering attacks. The consequences of a data breach can range from reputational damage to financial losses and legal liabilities.
Best Practices for Computer Security: Keamanan Komputer Menurut Para Ahli
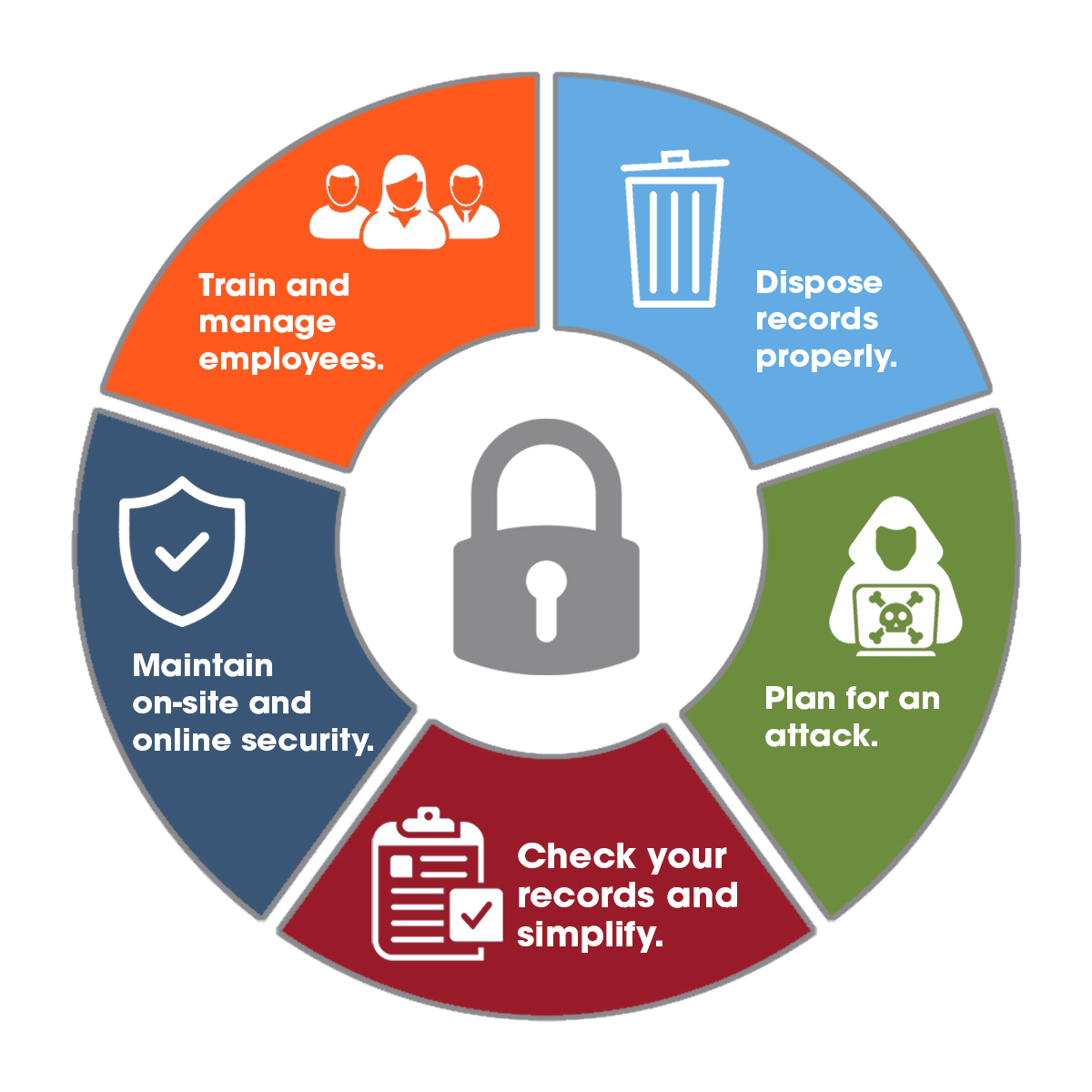
Maintaining robust computer security is crucial in the digital age. Implementing effective security measures safeguards sensitive data, protects systems from unauthorized access, and ensures the smooth functioning of computers and networks.
Individuals and organizations should adhere to the following best practices to enhance their computer security posture:
Strong Passwords
Strong passwords serve as the first line of defense against unauthorized access. They should be complex, containing a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable words or personal information.
Firewalls
Firewalls act as gatekeepers, monitoring and filtering incoming and outgoing network traffic. They block malicious attempts to access your computer or network by unauthorized entities.
Antivirus Software
Antivirus software scans for and removes malicious software, such as viruses, malware, and spyware. It provides real-time protection, preventing these threats from infecting and damaging your computer.
Regular Software Updates
Software updates often include security patches that address vulnerabilities and fix bugs. Regularly updating operating systems, applications, and software ensures that your systems are protected against the latest threats.
Backups
Regular backups create copies of important data, safeguarding it in case of hardware failure, data loss, or ransomware attacks. Storing backups on separate devices or cloud storage provides an additional layer of protection.
Cloud Security Considerations

Cloud computing offers numerous benefits, including scalability, cost-effectiveness, and flexibility. However, it also introduces unique security challenges due to the shared responsibility model and the distributed nature of cloud environments.To ensure the security of cloud infrastructure, data, and applications, it is crucial to understand these challenges and implement appropriate measures.
This includes implementing strong access controls, encrypting data both in transit and at rest, and regularly monitoring and patching systems.
Responsibilities in Cloud Security
In a cloud computing environment, the responsibility for security is shared between the cloud provider and the customer. The cloud provider is responsible for the security of the underlying infrastructure, while the customer is responsible for the security of their data and applications.
It is essential for both parties to understand their respective responsibilities and work together to maintain a secure cloud environment.
Emerging Trends in Computer Security
The realm of computer security is constantly evolving, with new threats emerging alongside innovative technologies designed to combat them. This section will explore some of the most pressing cybersecurity trends, examining their implications and potential impact on the future of data protection.
Artificial Intelligence (AI) and Machine Learning (ML) in Security
AI and ML are revolutionizing various industries, and their applications in cybersecurity are no exception. These technologies enable systems to learn from vast amounts of data, identify patterns, and make predictions, enhancing threat detection and response capabilities. For instance, AI-powered intrusion detection systems can analyze network traffic in real-time, flagging suspicious activities that might evade traditional rule-based systems.
Blockchain for Enhanced Data Protection
Blockchain technology, initially associated with cryptocurrencies, has gained traction in cybersecurity due to its inherent security features. Blockchain creates a distributed and immutable ledger, making it extremely difficult to tamper with data. This technology has the potential to revolutionize data protection by providing a secure and transparent way to store and manage sensitive information, reducing the risk of data breaches and unauthorized access.
Cybersecurity Frameworks and Standards
In the realm of cybersecurity, industry-recognized frameworks and standards serve as blueprints for safeguarding organizations from cyber threats. These frameworks provide a structured approach to identifying, assessing, and mitigating cybersecurity risks.
As cybersecurity experts emphasize the paramount importance of computer security, it’s crucial to delve deeper into the intricacies of this field. To gain a comprehensive understanding, refer to the informative presentation on cybersecurity . This presentation provides valuable insights into the latest threats, mitigation strategies, and best practices to safeguard our digital assets.
By staying abreast of these developments, we can effectively protect our computers and data from malicious actors.
Implementing cybersecurity frameworks like NIST (National Institute of Standards and Technology), ISO 27001 (International Organization for Standardization), and SOC 2 (Service Organization Control) offers numerous benefits. These frameworks establish best practices, enhance security posture, and streamline compliance efforts.
NIST Framework
NIST Cybersecurity Framework is a comprehensive guide that helps organizations manage cybersecurity risks effectively. It Artikels five core functions: Identify, Protect, Detect, Respond, and Recover.
NIST Framework provides a structured approach to cybersecurity risk management, enabling organizations to tailor their security measures to their specific needs and industry requirements.
ISO 27001, Keamanan komputer menurut para ahli
ISO 27001 is an international standard that specifies the requirements for an information security management system (ISMS). It provides a comprehensive set of controls and guidelines to protect the confidentiality, integrity, and availability of information.
Organizations that achieve ISO 27001 certification demonstrate their commitment to information security and compliance with international standards.
SOC 2
SOC 2 (Service Organization Control) is an auditing standard that assesses the security and privacy controls of service organizations that process customer data.
SOC 2 certification provides assurance to customers that the service organization has implemented appropriate security measures to protect their data.
Certifications and Compliance
Certifications and compliance with cybersecurity frameworks and standards play a crucial role in demonstrating cybersecurity maturity. These certifications provide independent validation of an organization’s security posture and adherence to industry best practices.
Achieving certifications like NIST CSF certification, ISO 27001 certification, or SOC 2 compliance can enhance an organization’s reputation, build trust with customers and partners, and gain a competitive advantage in the marketplace.
Ending Remarks
As technology advances, so too do the challenges of cybersecurity. Artificial intelligence, machine learning, and blockchain are transforming the security landscape, offering both opportunities and risks. By staying abreast of emerging trends and adopting industry-recognized frameworks, we can enhance our cybersecurity posture and protect our valuable data and systems.
FAQ Insights
What are the most common types of cyber threats?
Malware, viruses, phishing attacks, ransomware, and data breaches are among the most prevalent cyber threats.
How can I protect my computer from malware?
Install antivirus software, keep software up to date, and avoid clicking on suspicious links or opening attachments from unknown senders.
What is the role of cloud security?
Cloud security involves protecting data, applications, and infrastructure in cloud computing environments.
How can I improve my cybersecurity posture?
Implement industry-recognized cybersecurity frameworks, such as NIST, ISO 27001, and SOC 2, to enhance your cybersecurity maturity.