Keamanan siber dan privasi data merupakan masalah – In today’s digital age, cybersecurity and data privacy have emerged as critical issues, with businesses and individuals facing unprecedented threats to their sensitive information. This comprehensive guide delves into the multifaceted nature of cybersecurity and data privacy, exploring the challenges, regulations, best practices, and emerging trends shaping this complex landscape.
Cybersecurity Threats and Data Breaches
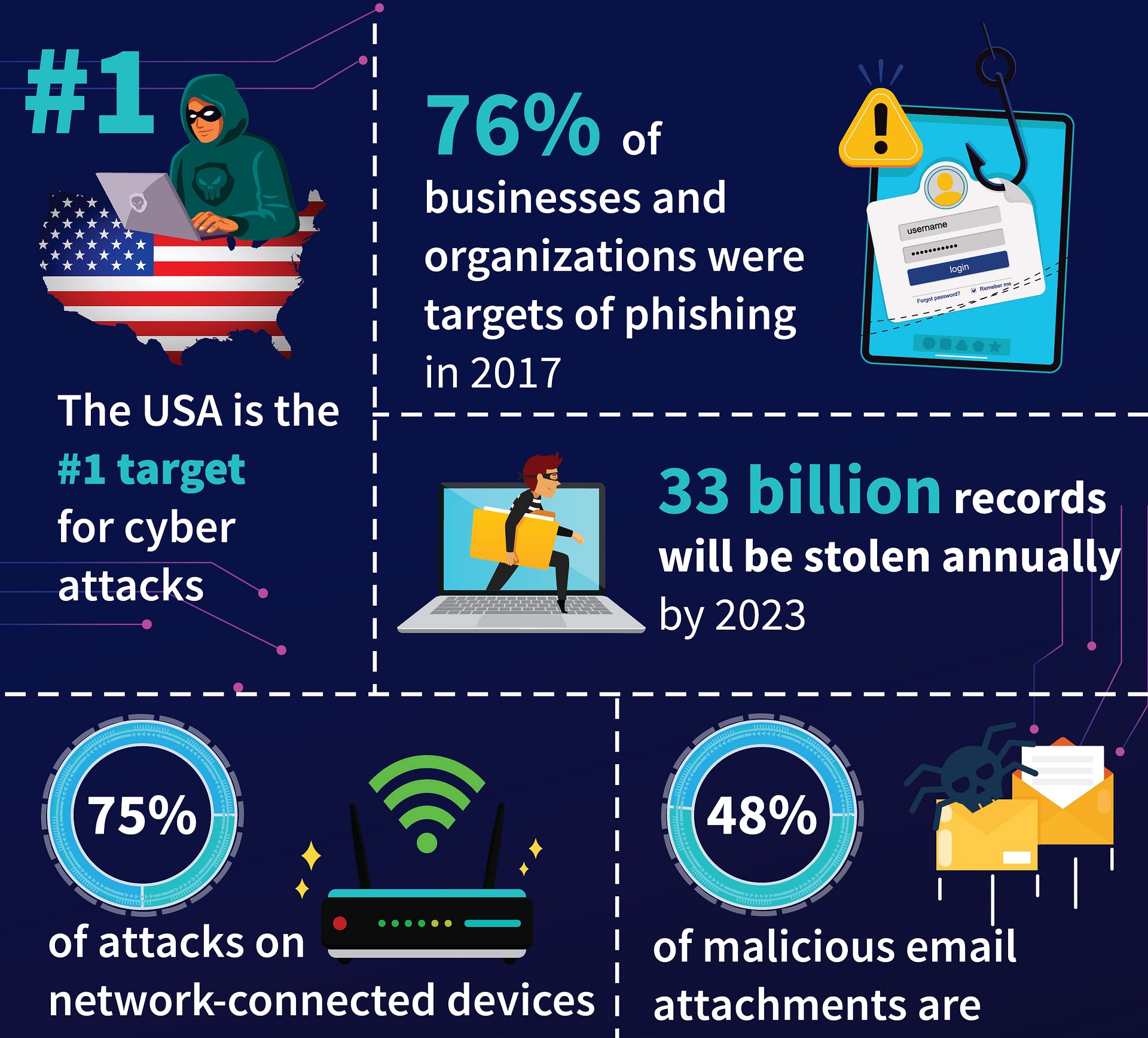
Cybersecurity threats pose significant risks to organizations, with data breaches becoming increasingly common. These threats range from phishing attacks to malware and ransomware, targeting sensitive data such as financial information, customer records, and intellectual property.
Major data breaches have occurred in recent years, including the Equifax breach in 2017, which compromised the personal information of over 145 million Americans. Such breaches have severe consequences for businesses, including reputational damage, financial losses, and legal liabilities. Individuals affected by data breaches face risks of identity theft, financial fraud, and other forms of cybercrime.
Types of Cybersecurity Threats
- Phishing Attacks:Attempts to trick individuals into providing sensitive information through fraudulent emails or websites.
- Malware:Malicious software designed to damage or disrupt computer systems, such as viruses, worms, and Trojans.
- Ransomware:Malware that encrypts data and demands payment for its release.
- Social Engineering:Exploiting human weaknesses to gain access to sensitive information or systems.
Data Privacy Regulations and Compliance: Keamanan Siber Dan Privasi Data Merupakan Masalah
In today’s digital age, protecting personal information is paramount. Data privacy regulations have emerged to safeguard individuals’ rights and ensure organizations handle sensitive data responsibly.
Key Data Privacy Regulations
- General Data Protection Regulation (GDPR):Applicable to organizations operating in the European Union, GDPR sets strict requirements for data collection, processing, and storage.
- California Consumer Privacy Act (CCPA):Similar to GDPR, CCPA protects California residents’ data and grants them rights to access, delete, and opt out of data collection.
- Health Insurance Portability and Accountability Act (HIPAA):Specifically designed for healthcare providers, HIPAA protects sensitive medical information from unauthorized access or disclosure.
Importance of Data Privacy Compliance
Complying with data privacy regulations is crucial for several reasons:
- Protects Personal Information:Regulations ensure organizations implement appropriate measures to safeguard personal data from unauthorized access, misuse, or data breaches.
- Builds Trust and Reputation:By adhering to data privacy laws, organizations demonstrate their commitment to protecting customers’ information, building trust and enhancing their reputation.
- Avoids Penalties and Fines:Non-compliance with data privacy regulations can result in significant penalties, fines, and legal consequences.
Implementing Effective Data Privacy Programs
Organizations can implement effective data privacy programs by following these guidelines:
- Conduct Data Audits:Identify all personal data collected, processed, and stored to determine potential risks and vulnerabilities.
- Develop Privacy Policies:Create clear and concise privacy policies that inform individuals about data collection, use, and sharing practices.
- Establish Data Security Measures:Implement appropriate technical and organizational safeguards to protect data from unauthorized access or disclosure.
- Provide Data Subject Rights:Comply with regulations that grant individuals rights to access, rectify, erase, and restrict the processing of their personal data.
- Monitor and Review:Regularly review and update data privacy programs to ensure ongoing compliance and effectiveness.
Best Practices for Cybersecurity and Data Privacy
Maintaining cybersecurity and safeguarding data privacy is crucial for organizations of all sizes. Implementing robust practices helps protect networks, prevent data breaches, and ensure compliance with regulations.
Cybersecurity and data privacy remain pressing issues, as evidenced by the recent news of SBY representing Akabri alumni in wishing Prabowo Subianto success in leading the nation SBY Wakili Alumni Akabri Doakan Prabowo Subianto Sukses Pimpin Bangsa . The rapid advancement of technology has brought about both opportunities and challenges, highlighting the need for robust measures to protect sensitive information and ensure online safety.
Network Security
- Firewalls:Software or hardware that monitors and controls incoming and outgoing network traffic, blocking unauthorized access.
- Intrusion Detection Systems (IDS):Monitors network activity for suspicious patterns and alerts administrators to potential threats.
- Virtual Private Networks (VPNs):Encrypts data transmitted over public networks, ensuring secure remote access.
Data Protection
- Encryption:Converting data into an unreadable format, making it inaccessible to unauthorized parties.
- Data Backup:Regularly creating copies of important data, ensuring its availability in case of data loss.
- Data Loss Prevention (DLP):Implementing policies and tools to prevent sensitive data from being accessed, used, or disclosed inappropriately.
Employee Training and Awareness
Employees are often the first line of defense against cybersecurity threats. Training and awareness programs are essential to educate employees on best practices, such as:
- Identifying and reporting suspicious emails or attachments.
- Using strong passwords and practicing good password hygiene.
- Understanding the risks of social engineering attacks.
Emerging Trends in Cybersecurity and Data Privacy

The realm of cybersecurity and data privacy is continuously evolving, with new technologies and threats emerging at a rapid pace. Artificial intelligence (AI), cloud computing, and the Internet of Things (IoT) are transforming the landscape, presenting both opportunities and challenges for organizations and individuals alike.
AI-powered cybersecurity tools are becoming increasingly sophisticated, enabling organizations to detect and respond to threats more effectively. Cloud computing offers greater flexibility and scalability for data storage and processing, but it also introduces new security risks that need to be addressed.
The proliferation of IoT devices is expanding the attack surface, making it essential for organizations to implement robust security measures to protect these connected devices.
Impact of AI on Cybersecurity
- Enhanced threat detection and prevention
- Automated incident response
- Improved threat intelligence
Impact of Cloud Computing on Data Privacy
- Increased data accessibility and flexibility
- Enhanced data security measures
- Potential for data breaches and privacy concerns
Impact of IoT on Cybersecurity
- Expanded attack surface
- Increased risk of data breaches
- Need for robust security measures
Future of Cybersecurity and Data Privacy
The future of cybersecurity and data privacy is likely to be characterized by:
- Continued advancements in AI and machine learning for threat detection and prevention
- Greater adoption of cloud computing and IoT devices, driving the need for robust security measures
- Increased focus on data privacy regulations and compliance
- Growing collaboration between organizations, governments, and individuals to address emerging threats
The Role of Technology in Cybersecurity and Data Privacy
Technology plays a vital role in protecting against cybersecurity threats and safeguarding data privacy. It provides various tools and techniques to detect, prevent, and respond to cyberattacks.
Benefits of Cybersecurity Tools and Technologies
- Enhanced Detection and Prevention:Cybersecurity tools, such as intrusion detection systems and firewalls, monitor network traffic and identify suspicious activities, preventing unauthorized access to systems and data.
- Data Encryption:Encryption technologies protect data from unauthorized access by encrypting it, making it unreadable without the appropriate decryption key.
- Multi-Factor Authentication:Multi-factor authentication requires users to provide multiple forms of identification, reducing the risk of unauthorized access to accounts and data.
- Automated Threat Response:Advanced cybersecurity tools can automate threat detection and response, minimizing the impact of cyberattacks.
Challenges of Cybersecurity Tools and Technologies, Keamanan siber dan privasi data merupakan masalah
- Complexity and Cost:Implementing and maintaining cybersecurity tools can be complex and expensive, especially for small and medium-sized organizations.
- False Positives:Cybersecurity tools can generate false positives, leading to unnecessary alerts and investigations.
- Evolving Threats:Cybercriminals constantly develop new and sophisticated attack techniques, requiring cybersecurity tools to be continuously updated.
- Human Error:Cybersecurity is not solely dependent on technology; human error can still lead to security breaches.
Future of Technology in Cybersecurity and Data Privacy
The future of technology in cybersecurity and data privacy is promising. Advancements in artificial intelligence (AI) and machine learning (ML) will enhance threat detection and response capabilities. Blockchain technology will provide secure and immutable data storage. Cloud computing will offer scalable and cost-effective data protection solutions.
Cybersecurity and data privacy are a growing concern in today’s digital world. As technology advances, so do the threats to our online security. Cybersecurity is crucial in protecting our personal information, financial data, and sensitive business secrets. By implementing robust cybersecurity measures, we can safeguard our digital assets and mitigate the risks associated with cyberattacks.
As technology continues to evolve, it will play an increasingly crucial role in safeguarding cybersecurity and data privacy.
Conclusion
As the world continues to evolve technologically, the importance of cybersecurity and data privacy will only increase. By understanding the threats, implementing effective measures, and staying abreast of emerging trends, organizations and individuals can safeguard their data, protect their reputations, and navigate the digital realm with confidence.
Helpful Answers
What are the most common types of cybersecurity threats?
Cybersecurity threats come in various forms, including malware, phishing attacks, ransomware, DDoS attacks, and social engineering.
What are the key data privacy regulations that businesses must comply with?
Data privacy regulations vary globally, but some notable examples include the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States.
What are the best practices for securing networks and protecting data?
Best practices for cybersecurity include implementing strong passwords, using encryption, installing firewalls and intrusion detection systems, and conducting regular security audits.


